02 prodiscover basic free download. Office2textile This project provides VBA add-ins which convert Microsoft Office contents to various text formats. . ProDiscover Basic installed on your workstation. FTK installed on your workstation. The GCFI-datacarve-NTFS.eve file you extracted to your work folder. In the following steps, you use ProDiscover to convert the image file to raw (.dd) format and then analyze the two images: 1. The ARC Group ProDiscover® Basic edition is a self-managed tool for the examination of your hard disk security. ProDiscover Basic is designed to operate under the National Institute of Standards’ Disk Imaging Tool Specification 3.1.6 to collect snapshots of activities that are critical to taking proactive steps in protecting your data.
The purpose of this lab is to try using Windows tools to examine Microsoft filesystem images to see what you can recover.
Autopsy as a tool for identifying whether pictures of Clint Eastwood are on a suspect drive
Prodiscover basic software. More Apple Software Update 2.6.3.1. 84.2MB - Shareware - Apple Software Update is a software tool by Apple that installs the.
In this investigation, we are continuing with our investigtion of Donald. We are attempting to ascertain whether he used the computer to get images of Clint Eastwood from the internet.
- Download Autopsy and install it, then run it
- Add the wholedrive image file from lab 1
- Use the evidence tree to view the filesystems found in the image, and explore them to see what files are in the image
- Clicking on a file in the file listing allows you to view a file. Use that ability to see if there are any pictures there of Clint Eastwood. If you find any, check the box next to the file with Clint Eastwood, and tag them as notable items.
- When you have examined all the pictures and tagged all the photos with Clint Eastwood in them, click Generate Report
- Create the report in html format
- Open the report by clicking on the file link and review it taking note of what the report contains, and what you would need to add to make it a complete forensic reportInclude the report in your submission for this lab.
Prodiscover Basic Tutorial
Using Prodiscover for identifying evidence of transactions between George Montgomery and Laura Roper
In this investigation, there is an allegation that Laura Roper and George Montgomery worked together. We are looking for evidence that will show whether they had an ongoing business relationship or not. An image file has been captured for us by a 3rd party. We have no access to the third party.
- Download a copy of Prodiscover Basic
- Install Prodiscover Basic and start it
- Start a new case
- Add the inChp02.eve image file extracted from InChp02.exe self-extracting zip file.
- Use the Search item in the Prodiscover navigation tree to try finding files with the words George, Montgomery, Laura, or Roper in them.
- Examine the contents of the found files to see if they do reference George and Laura and if they do, check them off as files of interest with suitable comments about what is in the files you found. Do not include files that aren’t relevant to both George and Laura together.
- Generate a report of your findings that describes the relationship between George and Laura and include that in your submission for this lab.
Finding Zone.identifier streams using Autopsy
- Start a new case
- Add the wholedrive image file you made last week
- Click in the evidence tree to select drive C, directory catfiles, so that the files show up in the file list on the upper right
- Repeat the previous step, but use the catfiles directory on drive D
- Include the following question with your answers in your submission for this lab.
- What extra files do you see on the D drive in the catfiles directory, compared to the C drive?
- What is in those extra files?
- How might you use that information as part of an investigation?
Examining the registry in an image file using AccessData Registry Viewer
If you have an image capture that includes the system.dat and user.dat files form the windows folder on a c: drive, you can examine the registry in that image. In this scenario, we are trying to determine if a captured registry from an employee’s computer has any information which might be useful to a paralegal investigating a Denise Robinson, who works for a competitor, Superior Bicycles.
- Begin by copying the two registry files to a temporary folder. For this lab, you can download some sample files.
- Extract the system.dat and user.dat files to a temporary folder.
- Now we are going to look for references to superior bicycles or denise robinson in the registry to see if they left tracks in the registry.
- Download the AccessData Registry Viewer and install it. When you start it, it will ask about a security device for licensing use, just choose No to run in Demo mode.
- Use File->Open to open the user.dat file you previously downloaded.
- Use Edit->Find and Edit->Find Next to find the string “superior” and the string “denise” in the registry image.
- Save a list of the registry keys you found and their contents, and include them in your sumission for this lab.
Submit a single PDF file containing your results of doing the 4 investigations in the lab instructions on github.
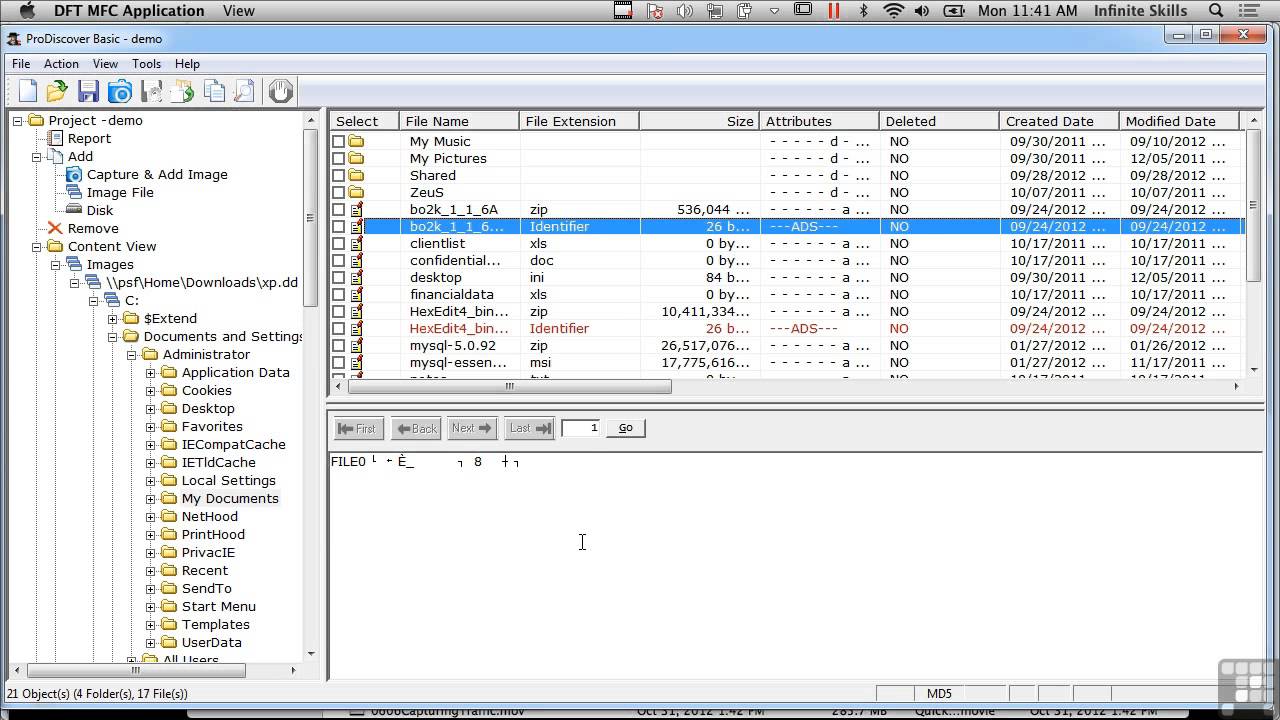
- For the first investigation, include the instructions, your activity notes, and a screenshot of the Autopsy window showing the tagged image file in the html report.
- For the second investigation, include the report of your findings.
- For the third investigation, include the 3 questions and your answers.
- For the fourth investigation, include either screenshots of the keys you found with their contents, or a copy-pasted list of them with their contents.
Our images are trivial. For more interesting images, you could try some of the example investigations detailed at http://dftt.sourceforge.net which is a site for some forensic tool testing.
Topics
- Imaging in Digital Forensics- Dead Imaging vs. Live Imaging
- Free Digital Forensic Investigation Tools and Live CDs For Digital Forensics
- File System Analysis: Windows
Imaging in Digital Forensics
Dead Imaging vs. Live Imaging
What Is Imaging?
- Working directly on the original evidence (e.g., hard disk of a computer) in any forensic data recovery operation or computer forensic investigation is not allowed as the investigation can make irrecoverable changes to the source data.
- Therefore, the first step is to create an exact duplicate of the media to be examined.
- Creating an exact copy of the original digital media that investigators can examine is commonly referred to as making a bitstream image or simply the imaging process.
- The image is just a file which can be handled easily.
- When imaging is done, a process called hashing generates a hash to ensure that the image and original media are the same.
Tools for Imaging
- A program called dd, which was originally a Unix utility.
- Various dd-based utilities such as dcfldd, which is also capable of generating hash at the end of process.
- Ftk Imager
- Sans SIFT
- Volatility
- ProDiscover Basic
- The Sleuth Kit
- Encase Forensic Imager
How Should We Image a Media?
- To guarantee that no change has would occur to the original digital media, using write blockers is recommended.
- Write blockers could be hardware or software.
- Hardware write blockers are normally preferred; however, they are not always available.
- Also, if the imaging were to be done on the original computer while it is powered, there is a chance of missing hidden data or getting interference during imaging from rootkits.
- The imaging therefore, can be done while the digital media is powered off and the media is outside the original computer. This process is known as dead imaging.
- Sometimes we have no choice and we have to image the media while it is connected and powered on. This process is known as live imaging.
Acquire Data by Live or Dead Imaging?
- It depends on the situation since each incident and the circumstances around it is unique. One of those is the type of data.
- In general, we have two types of data for investigation:
- Volatile data: This data will be lost when media is disconnected from power.
- Persistent data: This data remains intact after media is powered off. However, sometimes persistent data is stored using, for example, a full disk encryption solution and there is no access to the decryption key.
- As we explain the two types of imaging, the cases of using live vs. dead imaging is also discussed in the next few slides.
Dead Imaging
- Dead imaging is when the digital media (that is to be imaged) has been powered off and will be imaged outside of its original computer.
- This method is the preferred method since there is no chance to temper with data on the media during the imaging process.
- In other words, if dead imaging is performed properly, the chance of data alteration on the original media (and image) is zero.
- If there is a chance that time bombs could be activated on the computer to erase the content of the digital media, it is recommended to shut down the computer and perform dead imaging.
Live Imaging
- Live imaging is when the media of a computer is imaged while the media is still connected to the computer and powered on.
- There are certain situations in which live imaging has to be performed:
- Imaging RAM is an example of live imaging since powering off RAM would cause the loss of data in it.
- When a hard disk is encrypted and if it is powered off, all the data on it will be shielded from the investigator because of encryption. The issue is there is no access to the decryption key.
- When the responsible party may require that the system stay online for business reasons.
- If the data to be imaged resides in a remote location where physical access is limited or difficult.
- When there is a chance that powering off a disk or system may tip off an attacker or malicious process that it is being analyzed, causing a change in behavior that may hinder the investigation (Vandeven, 2014).
Deciding Between Live vs. Dead Imaging
- Dead imaging is always available to nonvolatile media.
- Live imaging of nonvolatile media is recommended based on the situation such as the chance of further changes to media or lack of accessibility due to encryption.
- Therefore, it is recommended to decide immediately whether to perform live imaging.
Imaging Best Practices
- In addition to use proper evidence-handling techniques in the event that the image is used as evidence in a courtroom, it is important to pay attention to the following tips.
- Use write blockers to prevent alteration of the evidence
- Use tested tools and techniques
- Check for disk encryption prior to removing power from the disk
- Perform live imaging if necessary before turning the machine off for dead imaging
- Consider logical volume or physical drive acquisition
- Encrypt forensic images for confidentiality
- Establish proper chain of custody for the image (Vandeven, 2014)
References
Hay, B., Nance, K., & Bishop, M. (2012). Live analysis: Progress and challenges. Computer.org. Retrieved from the UMUC digital library: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.226.6631&rep=rep1&type=pdf
Huber, M., Taubmann, B., Wessel, S., Reiser, H., & Sigl, G. (2016). A flexible framework for mobile device forensics based on cold boot attacks. EURASIP Journal on Information Security, 2016(1), 1-13. doi:10.1186/s13635-016-0041-4. Retrieved from the UMUC digital library: http://eds.b.ebscohost.com.content.umgc.edu/eds/pdfviewer/pdfviewer?vid=6&sid=ffdb366f-4fcf-449c-bd54-5e56c08c3e5d%40sessionmgr120&hid=113
Mahmood, T., Nawaz, T., Irtaza, A., Ashraf, R., Shah, M., & Mahmood, M. T. (2016). Copy-move forgery detection technique for forensic analysis in digital images. Mathematical Problems in Engineering, 2016,1-13. doi:10.1155/2016/8713202. Retrieved from the UMUC digital library: http://eds.b.ebscohost.com.content.umgc.edu/eds/pdfviewer/pdfviewer?vid=10&sid=ffdb366f-4fcf-449c-bd54-5e56c08c3e5d%40sessionmgr120&hid=113
Vandeven, S. (2014). Forensic images: For your viewing pleasure. SANS Institute.Retrieved from www.sans.org/reading-room/whitepapers/forensics/forensic-images-viewing-pleasure-35447
Free Digital Forensic Investigation Tools
And Live CDs for Digital Forensics

Common Investigation Cases Require Data
- an internal human resources case
- an investigation into unauthorized access to a server
- a series of file deletions
- malware spreading analysis
- or just to learn a new skill to be prepared for the above cases
What Would a Digital Forensics Data Acquisition Tool Do?
- Such tools can be used to extract data from inside different data sources to learn more about what’s “under the hood” of that source.
- Examine massive data sources such as memory, hard drive, USB drives, mobile devices, network and security devices’/tools’ logs, etc.
- By using these tools, you can image a hard-drive, or memory, or acquire data from mobile devices, etc.
- The tools can provide data carving and analysis of the raw data sources to extract evidence.
The following slides list some of the top available tools (Tabona, 2013).
ProDiscover Basic
- A digital forensic investigation tool to image, analyze, and report on evidence found on a drive.
- The data can be viewed by content or by looking at the clusters that hold the data.
- Data can be searched for specific information (Tabona, 2013).
Prodiscover Basic 8.2 Download
FTK Imager
- Tool by Access Data for data preview and hard drive imaging.
- It can mount a forensic image and can be viewed in Windows Explorer.
- Content of forensic images or memory dumps can be viewed.
- Files and folders on local hard drives, network drives, CDs/DVDs, etc. can be examined.
- Capable of creating SHA1 or MD5 hashes of files.
- Capable of exporting files and folders from forensic images to disk.
- Deleted files review and recovery from the Recycle Bin (Tabona, 2013).
DSi USB Write Blocker
- A software-based write blocker that prevents write access to USB devices. This can prevent modifying the metadata or timestamps and invalidating the evidence on a USB drive (Tabona, 2013).
USB Historian
- It can find and list USB information, primarily from the Windows registry, that were plugged into the machine.
- Displayed information includes the name of USB drive, its serial number, user-account mounted by and time/date of mount (Tabona, 2013).
Mandiant RedLine
- Memory and file analysis of a computer or device.
- It collects information about running processes and drivers from memory, and gathers file system metadata, registry data, event logs, network information, services, tasks, and Internet history to build a threat assessment profile (Tabona, 2013).
Volatility
- Memory forensics framework for incident response and malware analysis
- Digital artifacts can be extracted from volatile memory (RAM) dumps.
- Such artifacts include dynamic system behavior data such as running processes, open network sockets and network connections, DLLs loaded for each process, cached registry hives, and process IDs (Tabona, 2013).
Oxygen Forensics Suite (Standard Edition)
- Is a tool to collect evidence from a mobile device
- Capable of
- Finding device information (serial number, operating system)
- Contacts, messages (e-mails, multimedia messaging, etc.)
- Recovery of deleted messages, call logs, and calendar and task information.
- It also comes with a file browser to access and analyze user photos, videos, documents, and device databases (Tabona, 2013).
Free Hex Editor Neo
- A hex editor that can work with large files such as database files or forensic images.
- Can be used for manual data carving, low-level file editing, information gathering, or searching for hidden data (Tabona, 2013).
HxD
- A hex editor for low-level editing and modifying of a raw disk or main memory (RAM), and can handle large files.
- It can perform search and replacement, exporting, checksums/digests, file shredding, concatenation or splitting of files, and generation of statistics (Tabona, 2013).
Bulk_extractor
- A tool to scan a disk image, a file, or group of directory of files to extract information such as credit card numbers, domains, e-mail addresses, URLs, and ZIP files.
- The extracted information comes in form of text files (Tabona, 2013).
Xplico
- An open source network forensic analysis tool to extract applications data from Internet traffic (POP, IMAOP, SMTP)
- It supports many protocols such as HTTP, SIP, IMAP, TCP, UDP, TCP.
- Capable of TCP packet reassembly.
- Sends the extracted data to a MySQL or SQLite database (Tabona, 2013).
LastActivityView
- Use to view the last activities by (a) user(s) and events happened in a machine.
- Activities include running an executable file, opening a file/folder from Explorer, or an application or system crash or software installation by a user.
- The information can be exported to a CSV, XML, or HTML file (Tabona, 2013).
The Sleuth Kit (+Autopsy)
- It is an open source digital forensics toolkit for file systems analysis.
- Autopsy is a GUI wrapper for The Sleuth Kit.
- Capable of timeline analysis, hash filtering, file system analysis and keyword searching (Tabona, 2013).
SANS Investigative Forensic Toolkit (SIFT) (digital-forensics.sans.org/community/downloads)
- Ubuntu-based live CD.
- Suite of tools for forensic or incident response investigation.
- Supports analysis of Expert Witness Format (E01), Advanced Forensic Format (AFF), and RAW (dd) evidence formats.
- Has additional tools such as log2timeline for generating a timeline from system logs, Scalpel for data file carving, Rifiuti for examining the Recycle Bin, etc. (Tabona, 2013).
Computer-Aided INvestigative Environment (CAINE) (www.caine-live.net)
Prodiscover Basic 64
- Linux live CD.
- Includes a user-friendly GUI, semiautomated report creation and tools for mobile forensics, network forensics, and data recovery (Tabona, 2013).
PlainSight (http://www.plainsight.info/)
- A live CD based on Knoppix (a Linux distribution)
- Capable of performing digital forensic tasks such as viewing Internet histories, data carving, USB device information, physical memory dumps, and extracting password hashes (Tabona, 2013).
HELIX3 Free (2009R1)
- A live CD based on Linux that was built to be used in incident response, computer forensics and e-discovery scenarios. It includes hex editors, data carving, password cracking utilities, etc.
- The HELIX3 version 2009R1 is the last free version available (Tabona, 2013).
- (https://www.e-fense.com/store/index.php?_a=viewProd&productId=11)
Paladin Forensic Suite
- Ubuntu-based live CD with over 80 open source forensic tools.
- Categories including imaging tools, malware analysis, social media analysis, hashing tools, etc. (Tabona, 2013).
DEFT (www.deftlinux.net)
- Linux live CD for incident response, cyber intelligence and computer forensics scenarios.
- Includes most of the available forensics tools as well as tools for mobile forensics, network forensics, data recovery, and hashing (Tabona, 2013).
Free Digital Forensics Investigation Tools
| Investigation Tool | Resource Link |
|---|---|
| ProDiscover Basic | http://prodiscover-basic.sharewarejunction.com |
| AccessData FTK Imager | http://accessdata.com/product-download?/support/product-downloads |
| DSi USB Write Blocker | http://dsicovery.com/software/usb-writeblocker |
| USB Historian | http://www.4discovery.com/our-tools/ |
| Mandiant RedLine | https://www.fireeye.com/services/freeware/redline.html |
| Volatility | http://www.volatilityfoundation.org/24 |
| Oxygen Forensic Suite (Standard Ed.) | http://www.oxygen-forensic.com/en/ |
| Free Hex Editor Neo | http://www.hhdsoftware.com/free-hex-editor |
| HxD | https://mh-nexus.de/en/hxd/ |
| Bulk_extractor | http://www.forensicswiki.org/wiki/Bulk_extractor |
| Xplico | http://www.xplico.org/download |
| LastActivityView | http://www.nirsoft.net/utils/computer_activity_view.html |
| The Sleuth Kit (+ Autopsy) | http://www.sleuthkit.org |
| SIFT | https://digital-forensics.sans.org/community/downloads |
| CAINE | http://www.caine-live.net/page5/page5.html |
| PlainSight | http://www.plainsight.info/index.html |
| Helix3 Free | http://www.e-fense.com/products.php |
| Paladin Forensic Suite | https://sumuri.com/software/paladin/ |
| DEFT | http://www.deftlinux.net/download |
Reference
Tabona, A. (2013).Top 20 free digital forensic investigation tools for sysadmins. [Blog post]. TalkTechToMe. Retrieved from http://www.gfi.com/blog/top-20-free-digital-forensic-investigation-tools-for-sysadmins/?
File System Analysis: Windows
Windows Internals: SysInternals
- Sysinternals Suite is maintained by Mark Russinovich. The original Sysinternals Troubleshooting Utilities have been rolled up into a single suite of tools.
- This new file contains the individual troubleshooting tools and help files.
Some Disk Utilities of SysInternals
- Disk2vhd simplifies the migration of physical systems into virtual machines (p2v).
- DiskExt displays volume disk-mappings.
- The DiskMon utility captures all hard disk activity or acts like a software disk activity light in your system tray.
- DiskView is a graphical disk sector utility.
- NTFSInfo is used to find detailed information about NTFS volumes, including the size and location of the master file table (MFT) and MFT-zone, as well as the sizes of the NTFS metadata files.
Some Disk Utilities of SysInternals
- Sysmon (system monitor) is designed to run in the Windows system's background, logging details related to process creation, network connections, and changes to file creation time.
- Pend Moves is used to find files which are scheduled for delete or rename the next time the system boots.
- Process Monitor monitors file system, registry, process, thread and DLL activity in real time.
- PS File is used to see what files are opened remotely.
- Sdelete is used to securely overwrite your sensitive files and cleanse the free space of previously deleted files using this DoD-compliant secure delete program.
Sigcheck
Sigcheck is a command-line utility that shows file version number, timestamp information, and digital signature details, including certificate chains.
It also includes an option to check a file’s status on VirusTotal (https://www.virustotal.com/), a site that performs automated file scanning against over 40 antivirus engines, and an option to upload a file for scanning.
Sigcheck can be used to check for potential malware in an acquired image mounted as a read-only file system. For example, the contents of the Windowssystem32 directory of a mounted image file can be checked using sigcheck for all unsigned executable files.
Timeline Analysis of Windows Filesystem
- Timeline analysis is used to identify (or link) a sequence of events that is being investigated.
- Using the fls tool available with The Sleuth Kit (TSK, www.sleuthkit.org/), time-stamped information from an acquired image can be collected automatically.
- The result of the fls tool can be parsed further by the mactime Perl script to produce timeline information.
Open Resources
Bhardwaj, A., Avasthi, V., Sastry, H., & Subrahmanyam, G. V. B. (2016). Ransomware digital extortion: A rising new age threat. Indian Journal of Science and Technology, 9,14. Retrieved from http://s3.amazonaws.com/academia.edu.documents/46876570/Ransomware_Digital_Extortion_A_Rising__New_Age_Threat_INDJST.pdf?AWSAccessKeyId=AKIAJ56TQJRTWSMTNPEA&Expires=1476916432&Signature=HENwsU2xBBysENvOZUZTawlCqC0%3D&response-content-disposition=inline%3B%20filename%3DRansomware_Digital_Extortion_A_Rising_Ne.pdf
Russinovich, M. (2015). Process Explorer v16. 05. Retrieved from https://img.sauf.ca/pictures/2015-06-26/92aa6d0a7ed07fa9cb82c7bd9f02702e.pdf
Shaver, J. S. (2015). Exposing vital forensic artifacts of USB devices in the Windows 10 registry (Doctoral dissertation, Monterey, California: Naval Postgraduate School). Retrieved from http://calhoun.nps.edu/bitstream/handle/10945/45940/15Jun_Shaver_Jason.pdf?sequence=1&isAllowed=y
Shiaeles, S., Chryssanthou, A., & Katos, V. (2013). On-scene triage open source forensic tool chests: Are they effective? Digital Investigation, 10(2), 99-115. Retrieved from https://www.researchgate.net/profile/Stavros_Shiaeles/publication/236681282_On-scene_Triage_open_source_forensic_tool_chests_Are_they_effective/links/00b4953ac91d0d0086000000.pdf
Stormo, J. M. (2013). Analysis of Windows 8 Registry Artifacts. Retrieved from http://scholarworks.uno.edu/cgi/viewcontent.cgi?article=2794&context=td